Azure API Credentials
In order to integrate Security Phoenix with your Azure Defender for Cloud, you’ll need to authorise the platform to access Defender in your tenant and subscription(s). The following steps describe how to create the required API access credentials.
Create application and credentials
In your Azure Portal, navigate to Azure Active Directory for the directory that you want to integrate with. Then select “App registrations” in the left menu and click on “+ New registration” at the top.
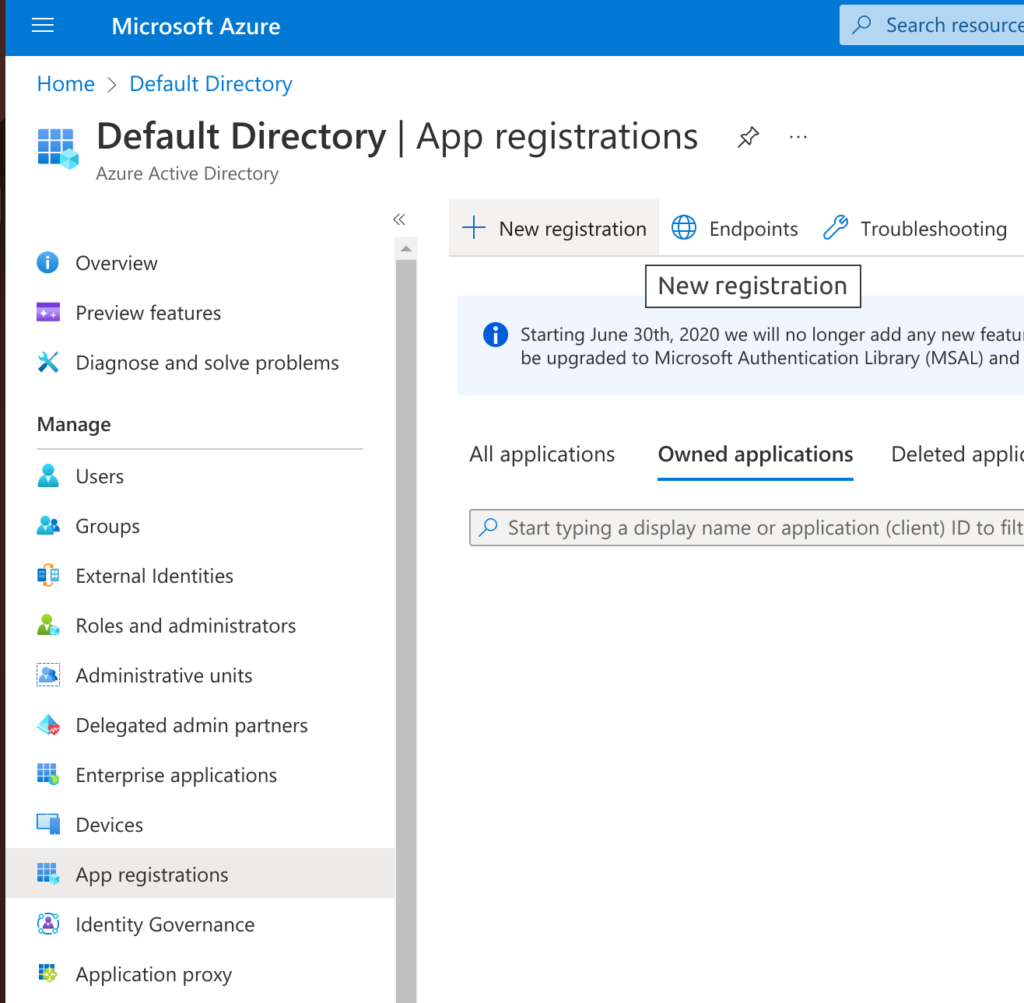
Enter a name for the application that will access Defender findings (e.g. “Phoenix Security”) and choose select the first option (“Accounts in this organizational directory only (Default Directory only – Single tenant)“) for “Supported account types”. Then click on “Register“.
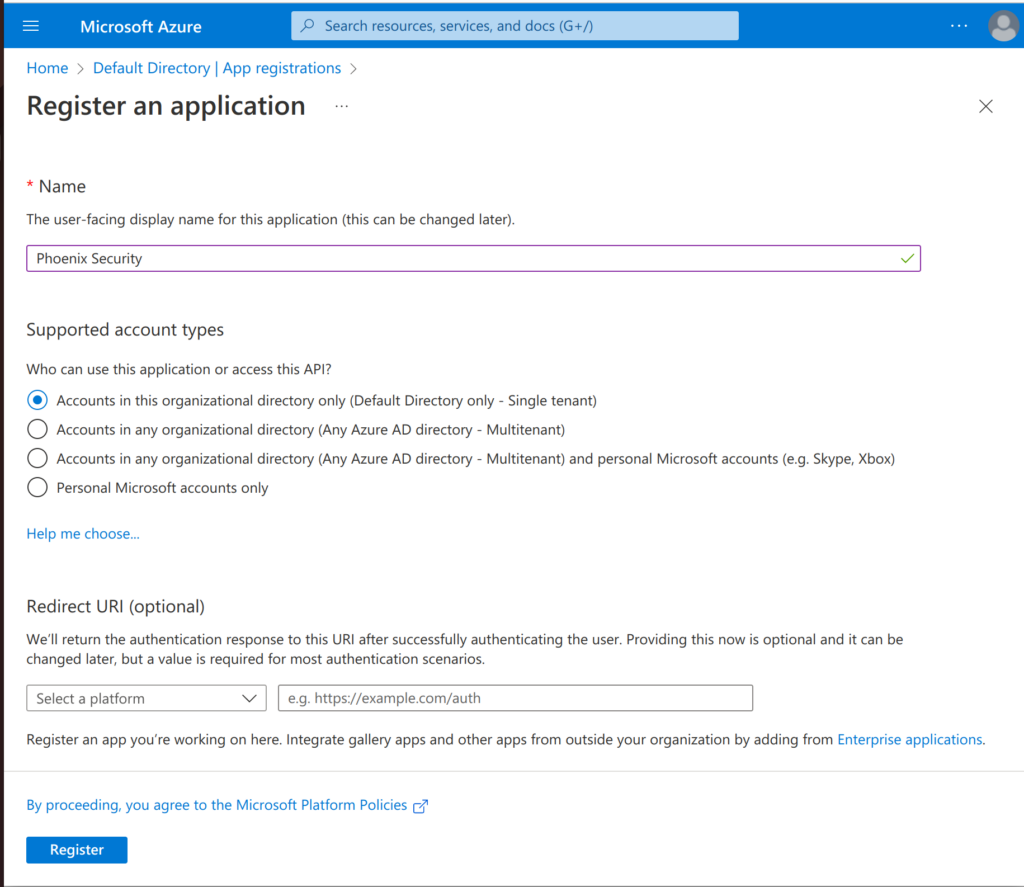
In the overview page (below) you will see the key details for this application (API access). You will need some of these details to configure access with Phoenix Security.
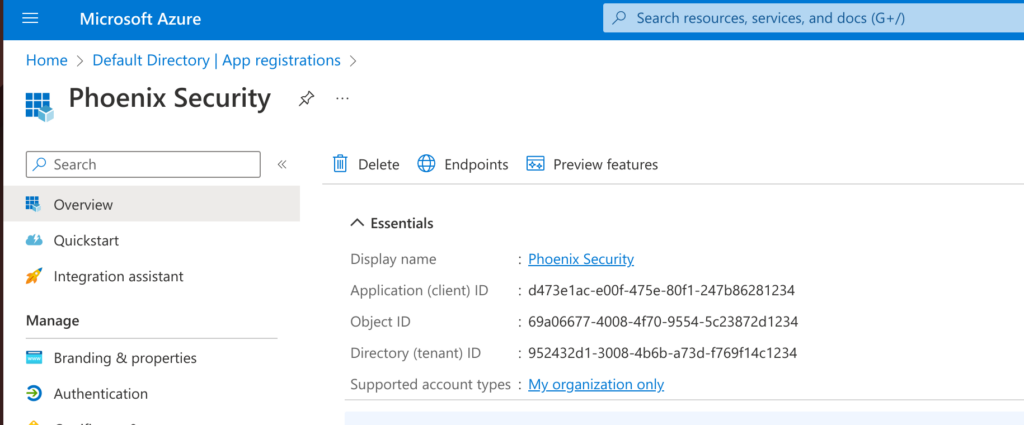
Now that you have your application, you just have to create a Secret so that it can authenticate with the API. Still within your registered application, click on “Certificates & secrets” and then within “Client secrets” select “+ New client secret“.
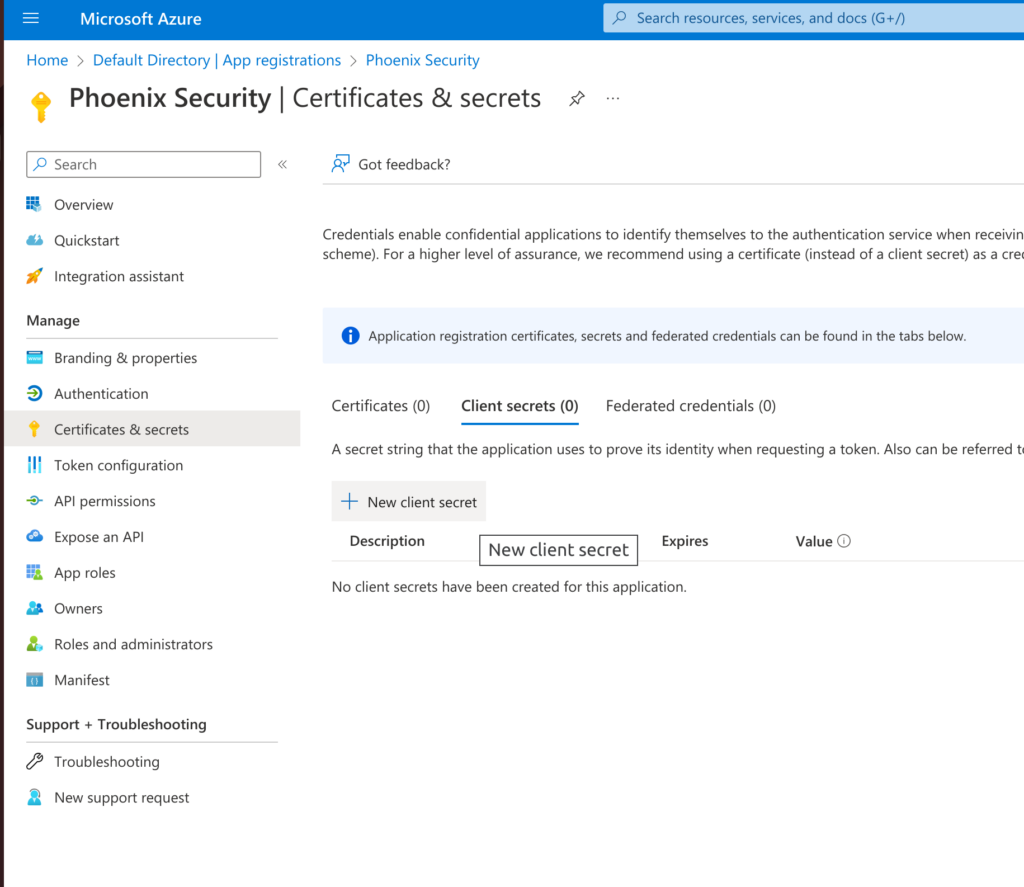
Give the secret a memorable name (e.g. “Phoenix Security API access”) and select a duration. Then clink on “Add“.
IMPORTANT: When you complete the creation you’ll be able to copy the secret’s Value; this is the last opportunity you’ll have to copy this value and keep it secure. You will need the secret as part of the Phoenix Security integration configuration.
Give Permissions to the Application
Now that you’ve created your application’s credentials, it’s time to define the level of access that those credentials would have.
Navigate to the Azure subscription that you want to provide access to. Select “Access control (IAM)” on the left menu and then click on “+ Add” and choose “Add role assignment”.

Search for the “Security Reader” permission, select it on the list and click “Next“.

The, under “Members”, click on “+ Select members” and search for the application created in the previous steps – e.g. “Phoenix Security”.
Then click on the application entry to select it, so that it appears at the bottom under “Selected members”; and click on the “Select” button. Continue to the “Review + assign” step to complete the role assignment.

Now repeat the same process for the “Reader” role.
The list of roles (filtered by the application name) should look like this:

Create an Azure Defender Integration
Within your Phoenix Security account, select Integrations > Scanners from the left menu and then click on “Add Scanner Integration” on the top-right corner.
Enter a name for this integration, select the Azure Defender scanner template and click on “Next“.

On the second step of the process, enter the credentials created in the first part of this guide.
- Server URL: Not required (only used for custom configurations)
- Tenant Id: “Directory (tenant) ID”
- Client Id: “Application (client) ID”
- Client Secret: Application secret’s Value

To finish the configuration click on “Create Scanner“. Unless there are issues with the credentials, the new scanner will appear in your list of integrations (under Integrations > Scanners) and the platform will start to collect asset and vulnerability details from all Subscriptions available through the integration credentials.
All these assets and vulnerabilities would be automatically added to your account’s Default Cloud Environment, and will be available to start assigning them to user Environments as required.

