Acunetix API Credentials
To integrate with the Acunetix API you need a valid set of User ID/Token. In order to do so, please follow the instructions below, which are a summary of the ones here.
- Log in to Acunetix 360.
- Select [Your Name] (top right of the page) > API Settings.
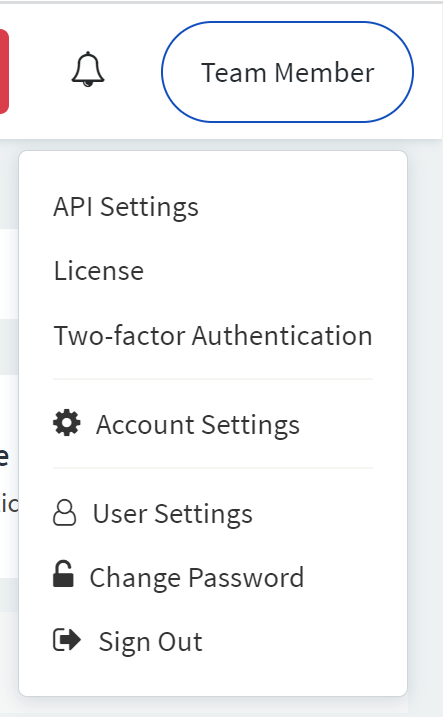
- In the Current Password field, enter your current password.
- Select Submit to view your User ID and Token.
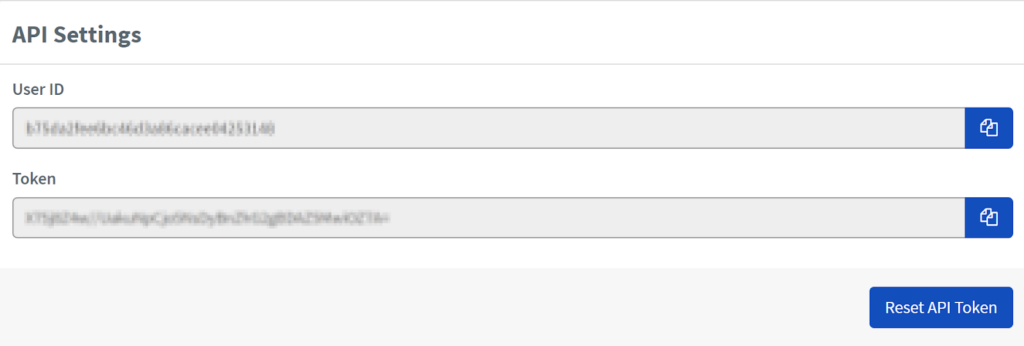
You will need the User ID and Token when configuring the integration between Phoenix Security and Acunetix.
Create a Acunetix Integration
- On the sidebar menu, navigate to the Scanners tab in the Integrations section.
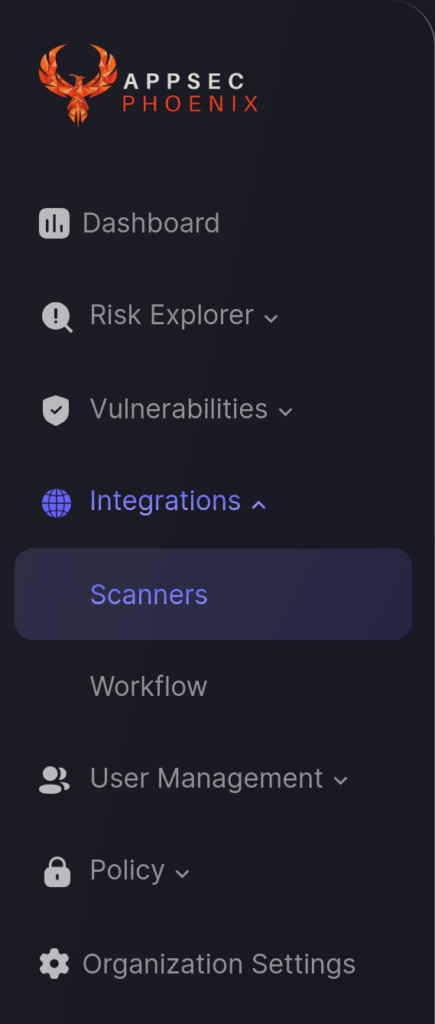
- Click on the “Add Scanner Integration” button on the right side of the page.
- In the first step, mouse over the Acunetix entry in the list of available integrations; then click the “Create Integration” icon (+).

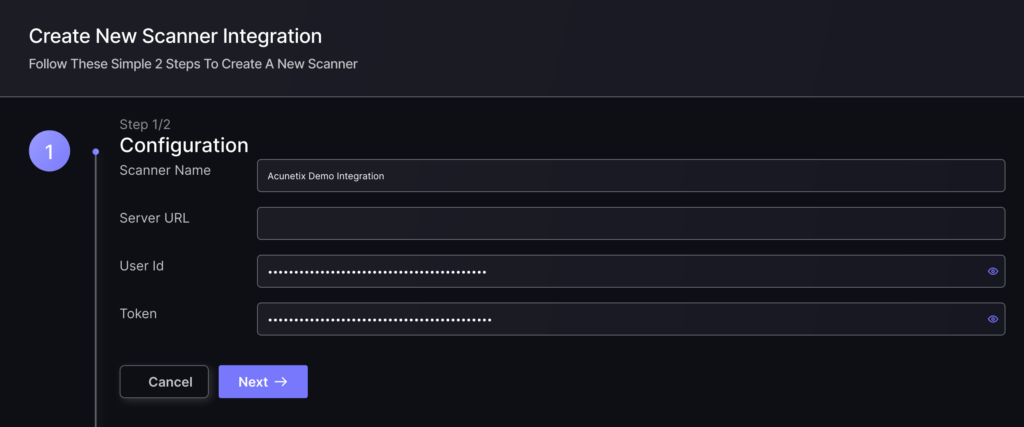
- On the second step you need to provide the required details for the scanner integration. In the case of Acunetix you need to provide:
- Name: The name for this integration.
- Server URL: This is optional. You only need to provide this if you know that your account’s API URL is different than the default (https://online.acunetix360.com).
- User ID: Enter the User ID obtained in the initial section above.
- Token: Enter the API Token obtained in the initial section above.
- In the next step you will be able to select whether the platform fetches all the assets and vulnerabilities available form the scanner, or you can include/exclude individual “targets” (applications, project, etc), if supported by the scanner.
- To finish the configuration click on “Create Scanner“.
Unless there are issues with the credentials, the new scanner will appear in your list of integrations (under Integrations > Scanners) and the platform will start to collect asset and vulnerability details from all Subscriptions available through the integration credentials.
All the scanner’s assets and vulnerabilities will be automatically added to your account’s Default Application, and will be available to start assigning them to user-created Applications as required.

