Checkmarx SAST Credentials
To integrate with Checkmarx SAST API you need a valid set of user credentials (username and password). It might be advisable to create a user dedicated to API access, which would make it easier to remove access in case of suspected compromise.
Apart from user credentials, you will need your API URL. This should be an HTTPS-based URL with a public domain name or a public IP address, plus any specific port used for the API.
Create a Checkmarx SAST Integration
- On the sidebar menu, navigate to the Scanners tab in the Integrations section.
- Click on the “Add Scanner Integration” button on the right side of the page.
- In the first step, enter a name for this scanner integration and select Checkmarx from the list of available integrations in the SAST section; then click “Next“.
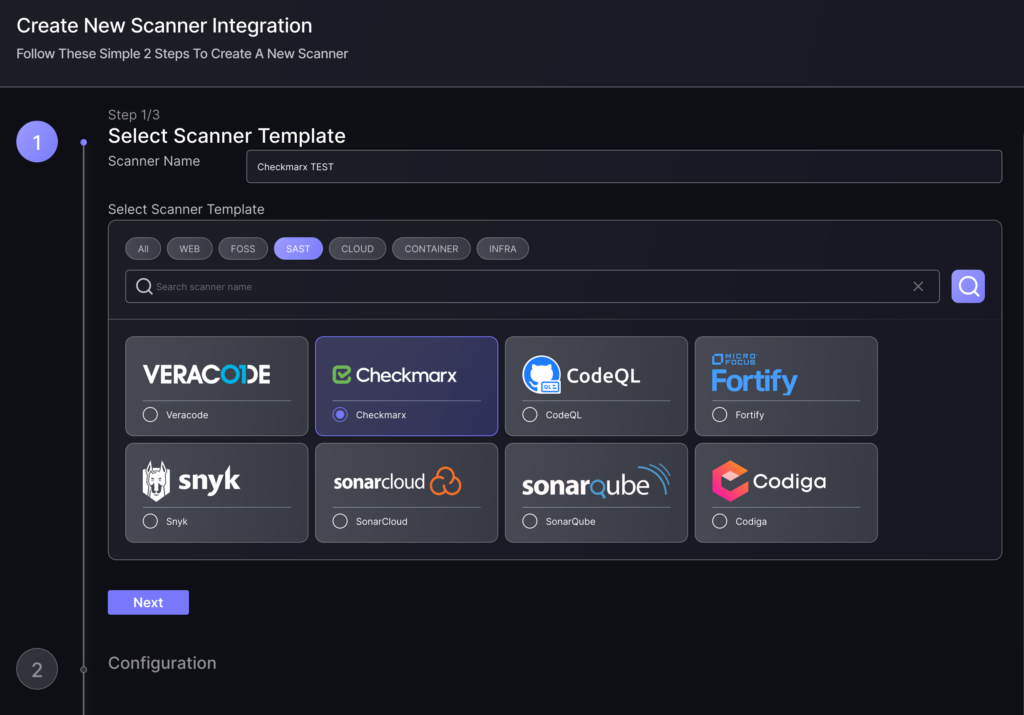
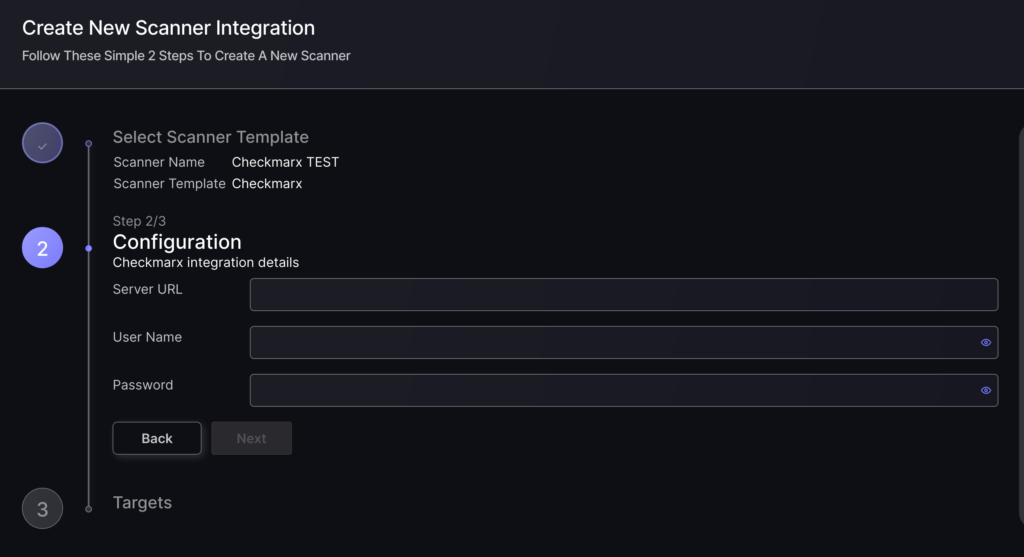
- On the second step you need to provide the required details for the scanner integration. In the case of Checkmarx SAST you need to provide:
- Server URL: Your API URL as described above.
- Username: Enter the username for the user credentials selected to access the API.
- Password: Enter the password for the user credentials selected to access the API.
- In the next step you will be able to select whether the platform fetches all the assets and vulnerabilities available form the scanner, or you include/exclude individual “targets” (applications, project, etc), if supported by the scanner.
- To finish the configuration click on “Create Scanner“.
Unless there are issues with the credentials, the new scanner will appear in your list of integrations (under Integrations > Scanners) and the platform will start to collect asset and vulnerability details from all Subscriptions available through the integration credentials.
All the scanner’s assets and vulnerabilities will be automatically added to your account’s Default Application, and will be available to start assigning them to user-created Applications as required.

