This article will show you how to add users and gives a breakdown of different user roles.
The User settings section allows administrators to manage user access and control according to organisational roles and to ensure user details are up to date. There is a table displaying each user’s details, including name, email, role, and the teams they are part of. It also shows whether a user’s account is active, enabling administrators to monitor access and ensure that only authorised personnel can use the system functions aligned with their roles.
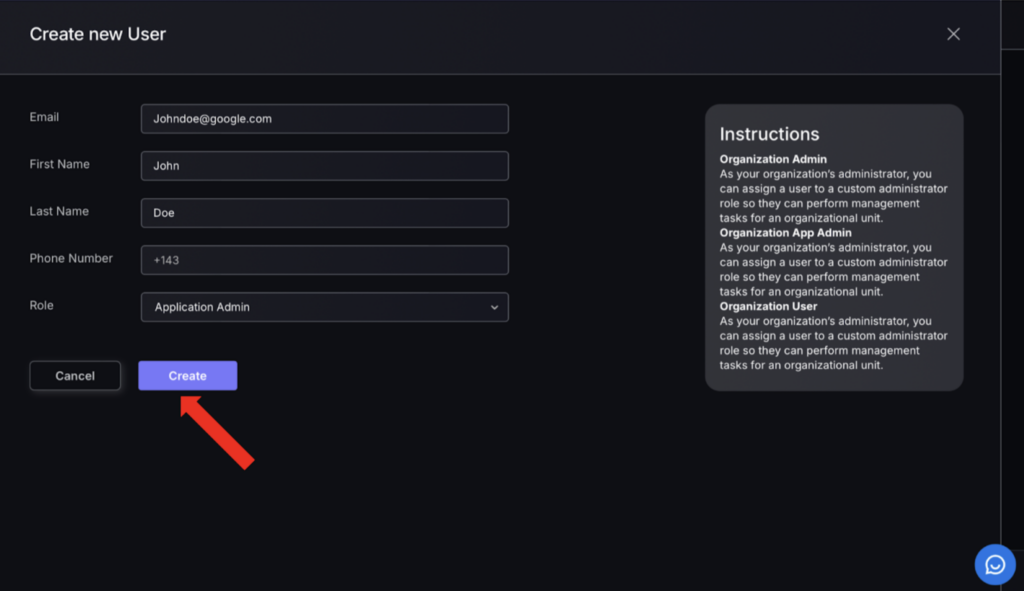
Additionally, there is an option to add new users, which will open a pop up requiring user details to be entered.
To add a new user follow these steps:
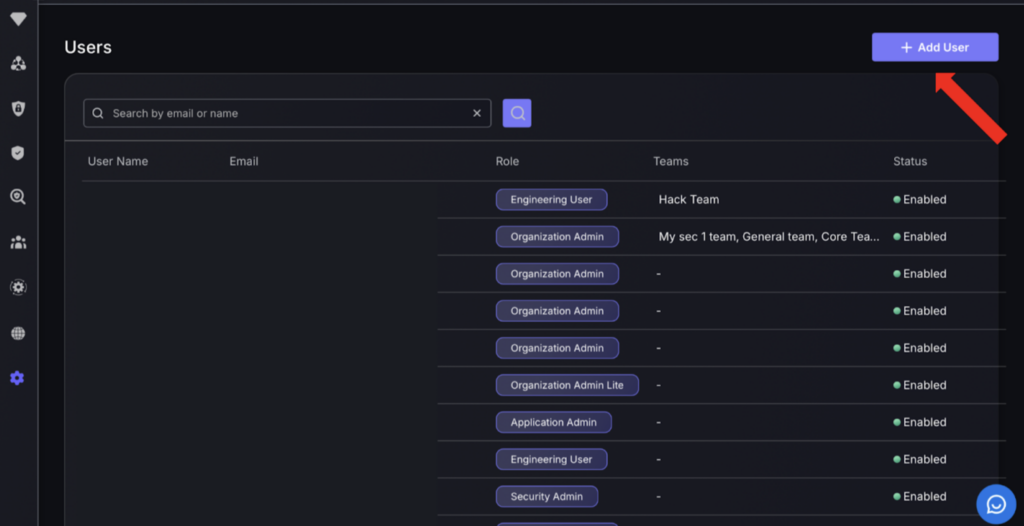
- Click the “Add User” button in the top right hand corner.
- Enter details:
- Email – Enter user email (used to send updates).
- First Name – Enter users first name.
- Last Name – Enter users last name.
- Phone Number – Enter users phone number (used to send alerts).
- Role – Select appropriate user role.
User Roles
Each user can be assigned to one of the following roles:
a. Organisation Admin – a super administrator role that has the highest privilege and access to all Phoenix Security features across all Applications. The Organisation Admin can manage Applications, Components, Environments, Vulnerabilities, Organisation Settings and Users.
b. Organisation Admin Lite – provides the same privileges as Organisation Admin but without User Management.
c. Organisation App Admin – an administrator role that provides admin privileges on a specific Applications only.
d. Application Admin – an administrator that has access and permission to edit their Application pages.
e. Engineering user – visibility limited to the Applications and Environments within the scope of the user’s teams (except when the user is not assigned to any team, they then have full visibility). User is able to propose risk exceptions and open tickets but not modify anything else in the platform.
f. Security Admin – an administrator with the ability to approve security exceptions.
g. Security champion – engineering role able to propose risk exceptions and open tickets but not modify anything else in the platform.
User Status
In addition to user roles, users can also have one of the following statuses:
a. Enabled – user is an active user and can log on to Phoenix Security.
b. Disabled – user is deactivated and cannot log on to Phoenix Security.
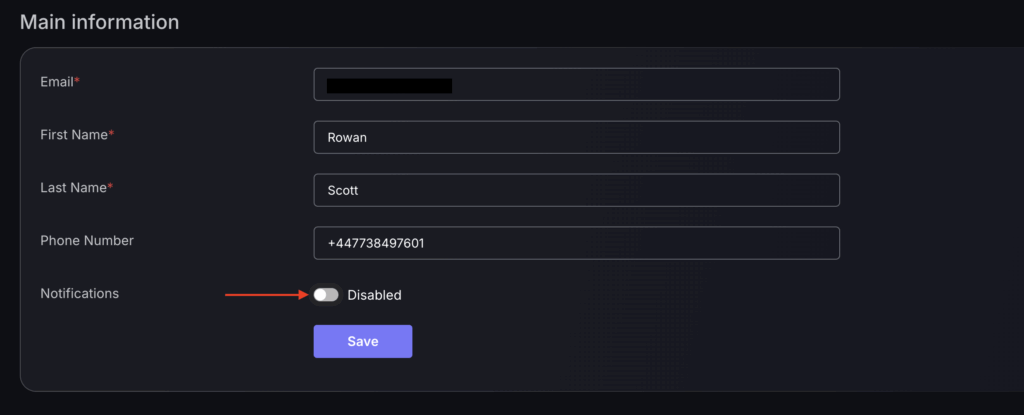
How to Enable/Disable Notifications
Phoenix provides automated notifications when a user enables them. These are set up depending on user roles to give you updates on what you are responsible for, e.g. a report of your top 10 Applications ranked by criticality for Organisation Admin roles, and any important updates to your organisation, such as failing scanners.
The notification configuration is found within your user profile.
- Click on your initials on the top right hand side of the page and select “Profile”.
- Then navigate to notifications under the main information section.
- Select the toggle so it says Enabled
- Press save