It is essential to ensure that the risk formula is correctly configured to a suitable setting for your organization.
Here are the steps to configure your risk profile:
- Scroll down to Settings on the navigation bar, and then press Organisation Settings.
- Press configuration.
- Scroll down to the Risk Configuration section and press Show Advanced Assets Configuration.
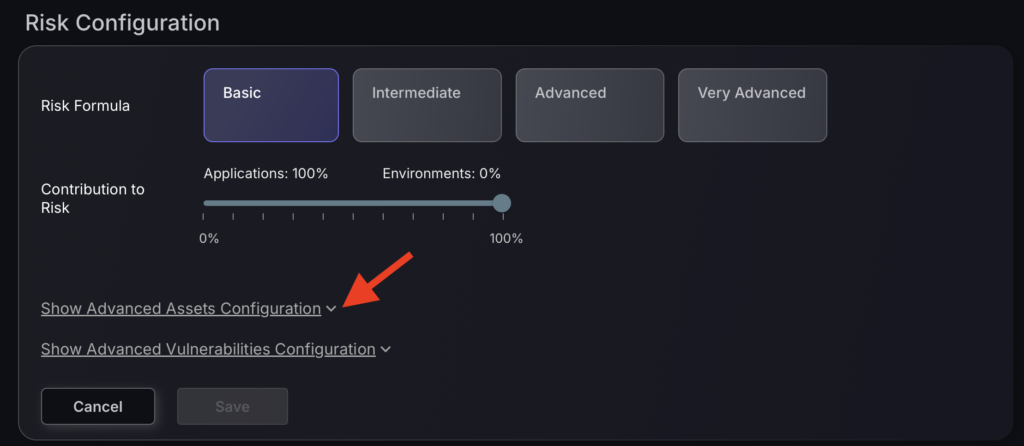
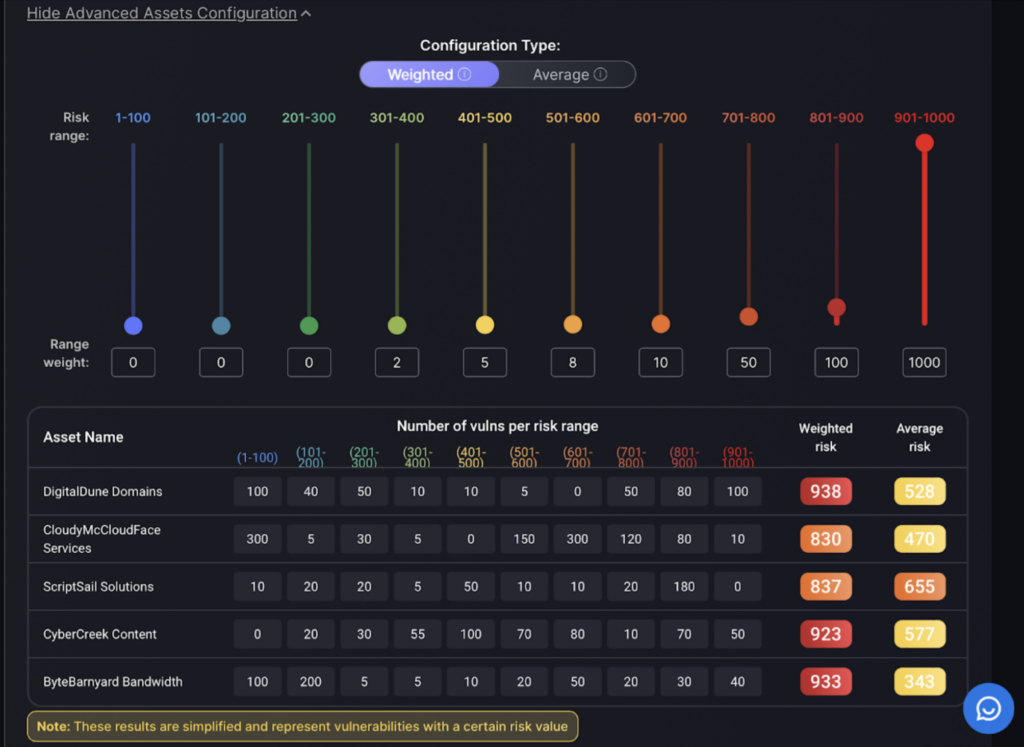
Advanced Assets Configuration
Adjustments in this section affect how risk is visualized and managed. If the risk configuration isn’t aligned correctly with a suitable security posture, it could lead to a misinterpretation of the risk levels. For instance, a misconfigured weight might exaggerate the risk of minor vulnerabilities or understate the importance of critical ones, leading to skewed risk management priorities. Proper calibration ensures that resources are allocated efficiently to address the most significant risks first.
Recommended Configuration for high risk prioritization:
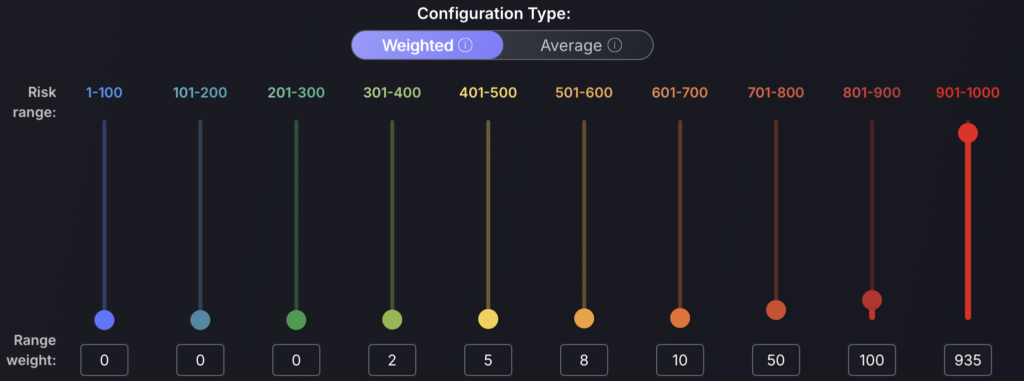
Highly exploitable vulnerabilities have an increased risk magnitude and are made a priority, while less exploitable/severe vulnerabilities risk scores remain the same. This will ensure vulnerabilities of higher severity/risk can be identified easily and fixed by engineering teams quickly and effectively.
Recommended Configuration for rounded prioritisation:

There is still prioritization of high-risk/highly exploitable vulnerabilities, but more prioritization is needed for less severe vulnerabilities that still pose a threat.
Bad configuration:
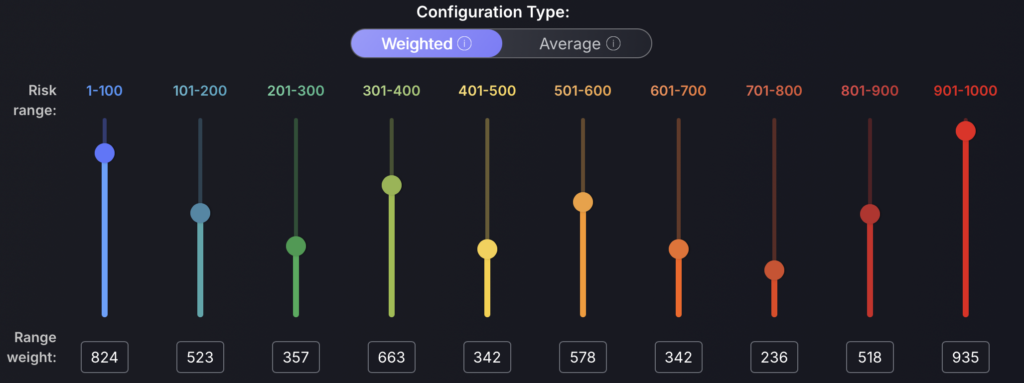
This configuration profile will lead to inconsistent risk scores. It is recommended that an exponential increase is made.
Linear Configuration in this settings the asset risk is influenced by all the vulnerabilities that it contains



